DNS Records and Record Types: Some Commonly Used, and Some You Might Not Know About
DNS is the system that associates domain names with IP addresses, so whenever we type in “securitytrails.com”, DNS uses a series of protocols to connect us with the authoritative DNS server of the domain name and serves us the content we intended to visit. DNS is one of the most popular internet services, and at the same time, is vulnerable to DNS-based attacks. Understanding DNS is an important step to prevent DNS attacks.
DNS servers contain one critical component: the DNS zone file. This file contains a variety of DNS records, each of which contains specific instructions for other servers to follow in order to connect to different services on the domain, such as the web server to visit a website or a mail server.
Most domain owners and users are familiar with “standard” DNS record types such as the A record, CNAME, MX and TXT records, as they are responsible for the everyday actions of online users. But beyond those more commonly used is an amazingly large list of DNS record types many users haven’t heard of.
Let’s refresh our knowledge about the most common DNS record types, and go over a list of all other, lesser-known ones in use today.
What are DNS records?
As mentioned, DNS records are essentially the instructions found on authoritative DNS servers and stored in their zone file. All domains need to have the few necessary records that allow a user access to a website, but there are many different DNS records involved. These include mail records, website records and informational records, among others. If you’re interested in learning more about the inner workings of DNS, check out our DNS root servers post.
Each DNS record has different components: the domain name; time to live (TTL), i.e. the time in seconds in which the client can store the record in cache before the information must be requested again from the DNS server; class, which is set to IN (internet) for common DNS records that involve hostnames, servers or IP addresses; the record type; and the type data, which is the information according to which the domain can be resolved. All of these components of the DNS record are structured in the DNS record syntax, which typically follows the format:<name> <ttl> <class> <type> <rdlength> <radata>.
Thus, a DNS record for the website.com web server will then look like this:www.website.com. 14000 IN A 192.158.1.38
Record types are of high interest, as they indicate the format of the data in the record and instruct on its intended use—for example, the MX record that contains the location of the mail server.
Most common DNS record types
Since the early days of DNS, the internet has morphed and advanced in such a way that DNS record types have constantly changed right along with it. Many have become obsolete, only to be replaced with newer types.
Some of the most common DNS record types are:
A record
A records are among the simplest and most fundamental DNS record types. The “A” stands for “address” and when you want to visit a website, send an email or, really, do anything on the internet, the domain you enter needs to be connected with the associated IP address. A records indicate the IP address for the given domain.
An example of an A record would look like:
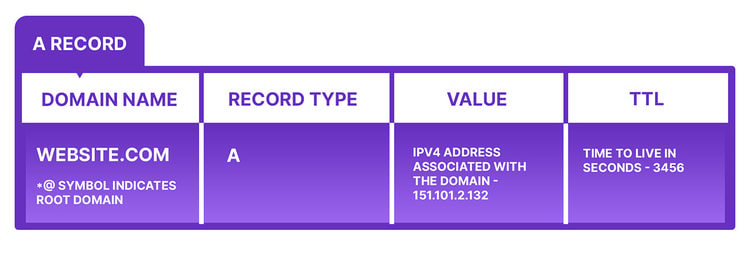
For example, if you enter “securitytrails.com” the A record will point you to the 151.101.2.132 IP address, essentially connecting your device with our website. Most websites have a single A record, but you can use multiple A records for the same domain to provide redundancy, or use a number of domain names that each have an A record pointing to the same IP address. Something important to know about A records is that they only contain IPv4 addresses.
AAAA record
What A records are to IPv4 addresses, AAAA records are to IPv6 addresses. These records contain the IPv6 address for a given domain name. And one important difference between IPv4 and IPv6 addresses is that IPv6 addresses are longer.
Here’s an example of an AAAA record:
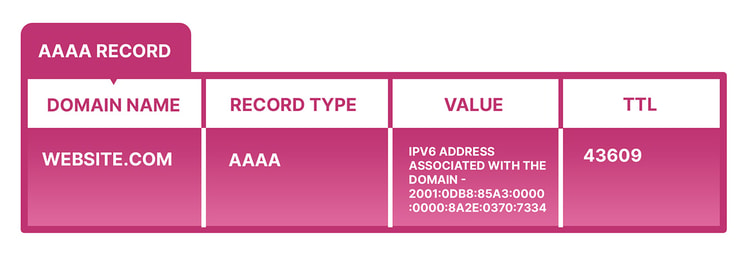
They represent the new version of the Internet Protocol and because the number of available IPv4 addresses is rapidly decreasing, it’s expected that IPv6 adoption will only grow. While all domains on the internet have one or more IPv4 addresses, not all have an IPv6 address, but that is also expected to change in the following years.
CNAME record
The CNAME record (or the “canonical name” record) maps an alias to a canonical domain name. It’s used as a replacement for an A record when a subdomain or a domain is an alias for another domain. CNAME records must always point to a domain as they do not provide an IP address.
Example of a CNAME record:
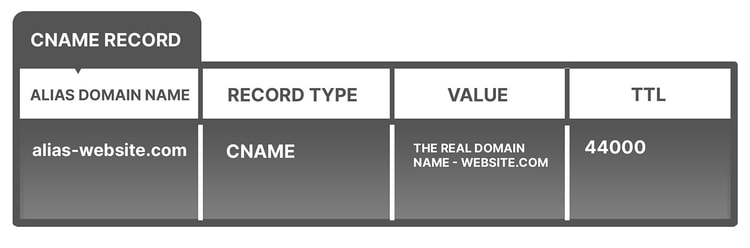
When websites have subdomains such as blog.website.com or careers.website.com, those subdomains will have CNAME records that point to the root domain, website.com. Because they don’t contain IP addresses, If an IP address of the root domain has to be updated, the CNAME records will still point to the domain. CNAME records also usually contain subdomains that point to an A or AAAA record meaning that there is no need to create an A or AAAA record for each subdomain.
MX record
The DNS MX or mail exchange record is responsible for directing an email to a mail server. The MX record instructs how an email message should be handled and like CNAME records, it always has to point to another domain. Common MX hostnames you’ve probably noticed are mail.website.com, smtp.website.com and imap.website.com.
An MX record will look like this:
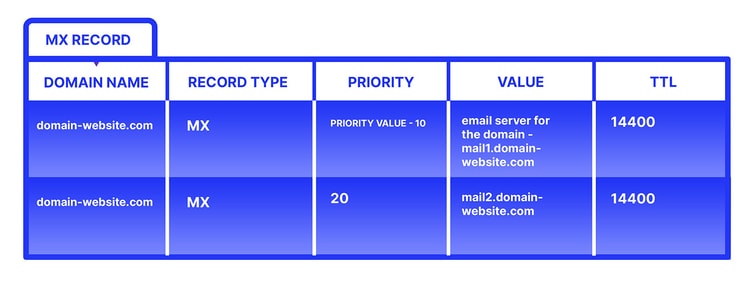
A domain can have multiple MX records, and usually we at least see MX records in use to offset a failure. When multiple MX records are used, they’re labeled by priority—the higher the priority value, the lower the priority. The highest priority (lowest priority value) MX record is connected to first, and other priority MX records will follow in a sequence based on their priority value—if they can be reached. So mailhost 2 will be connected only if mailhost 1 is not available.
NS record
The “NS” in NS records stands for “nameserver”. A nameserver is a type of a DNS server that stores all DNS records for a domain, including A, MX and CNAME records. An NS record contains information over which a DNS server is authoritative for the given domain. Put simply, when trying to access a domain, NS records will show where its IP address is.
Here’s an example of an NS record:
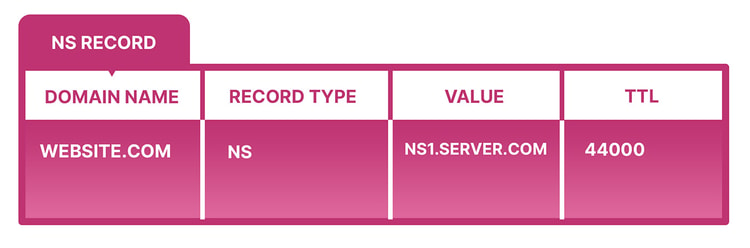
A domain often has multiple NS records that contain the same information and are used for redundancy. If one nameserver is unavailable, DNS will query another, backup nameserver. And without properly configured NS records, users wouldn’t be able to access a website, which can happen when a domain’s nameservers are changed and NS records aren’t updated to reflect it.
PTR record
A PTR, or Pointer, record acts as a reverse of A and AAAA records. Whereas A and AAAA records provide the IP address associated with a given domain, PTR records provide the domain name associated with an IP address. As such, DNS PTR records are used in reverse DNS lookups. With a reverse DNS lookup, the DNS server provides information about which hostnames belong to a specific IP address, as for every IP address in an A or AAAA record, there is a corresponding PTR record.
PTR records are stored under the IPv4 address in reverse, with “.in-addr.arpa” added because it’s a namespace within the .arpa top-level domain where PTR records are stored. For example, a PTR record for the 192.158.1.38 IP address would be stored under “38.1.158.192.in-addr.arpa”. For IPv6 addresses, PTR records are in a different namespace within .arpa and are stored under the IPv6 address, reversed and converted into 4-bit sections with “ip6.arpa” added.
Most commonly, we see PTR records used for anti-spam. Many email spam filters use reverse DNS to check the PTR record that comes with the email. They do this to see if the mail server sending the message matches the IP address it claims to be using, and if it’s associated with IP addresses likely to be used by legitimate email servers.
SOA record
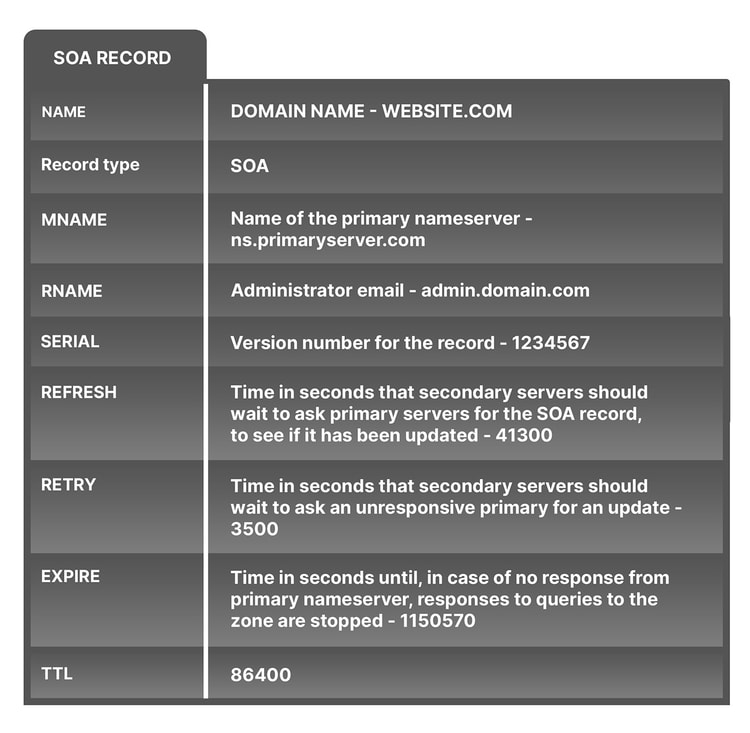
In DNS, a zone is an area of control over a namespace. It can include a single domain, or multiple domains and subdomains. A DNS zone file of every domain needs to contain an SOA or Start of Authority record. This is required for every DNS zone by IETF standards as SOA records are used in DNS zone transfers—the periodic process of distributing DNS record data from a primary to secondary nameserver, which contains the duplicates of the zone’s DNS records. The SOA record is transferred first, and its serial number signals the secondary nameserver that its version needs updating.
SOA records hold crucial information about a domain or zone, such as the name of the primary nameserver for the zone email address of the administrator, when the domain was last updated, and refresh and retry rules for secondary servers.
SOA records are much larger than other records, in the sense that they have a lot more components in them:
SRV record
An SRV record, or service record, stores host and port information for specific online services such as email, voice over IP (VoIP), instant messaging and the like. Unlike other DNS record types that specify a server or an IP address, SRV records include a port at the IP address where it needs to be reached. SRV records are used as a way to specify a port within the DNS, and some internet protocols such as IMAP, SIP and XMPP require SRV records as they need a specific port in order to function.
SRV records contain plenty of information, as seen in this example:
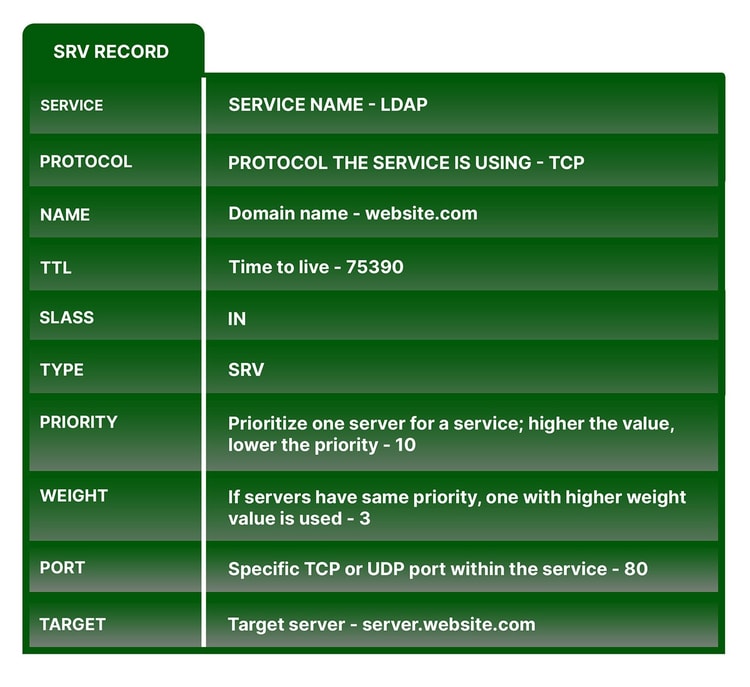
However, SRV records are actually formatted like this:
_service._protocol.name. TTL class type of record priority weight port target.So an SRV record, using our example from above, would look like this:
_ldap._tcp.website.com. 75390 IN SRV 10 3 80 server.website.com.TXT record
TXT records are DNS’s text records, which allow domain administrators to enter text into the DNS. While originally intended only for entering human-readable notes, today it’s possible to input some machine-readable data into TXT records.
A TXT record looks like this:
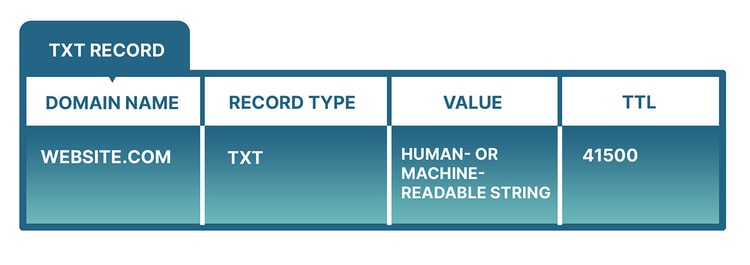
TXT records are mostly used for preventing email spam. These DNS records are used as part of several important and widely used email authentication methods to determine whether an email is coming from a trusted source. These mail authentication methods are Sender Policy Framework (SPF), Domain Keys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting and Conformance (DMARC). Using these records allows domain administrators to authenticate emails, so spammers can have a harder time spoofing their domains.
SPF was once a record on its own, but it was deprecated and is now only published as a TXT record. These records specify all the mail servers that are authorized to send emails from a domain. SPF alone is limited in detecting a forged sender, so it’s used in combination with DMARC.
DKIM works by signing each email with a public-private key pair, with the public key hosted in the TXT record associated with the domain. This allows for verification that the email is coming from the domain it claims to be from.
DMARC is a technical specification published in the TXT record that is used to authenticate an email by aligning SPF and DKIM policies.
Other DNS record types in use
A list of commonly used DNS record types barely hints at the plethora of other DNS record types in use, albeit less frequently. While new records are continually created, records are getting deprecated and replaced with newer ones at the same speed. The current list of every DNS record type, including obsolete ones, can be found on the official IANA website.
Here are other DNS record types in use at the time of this writing:
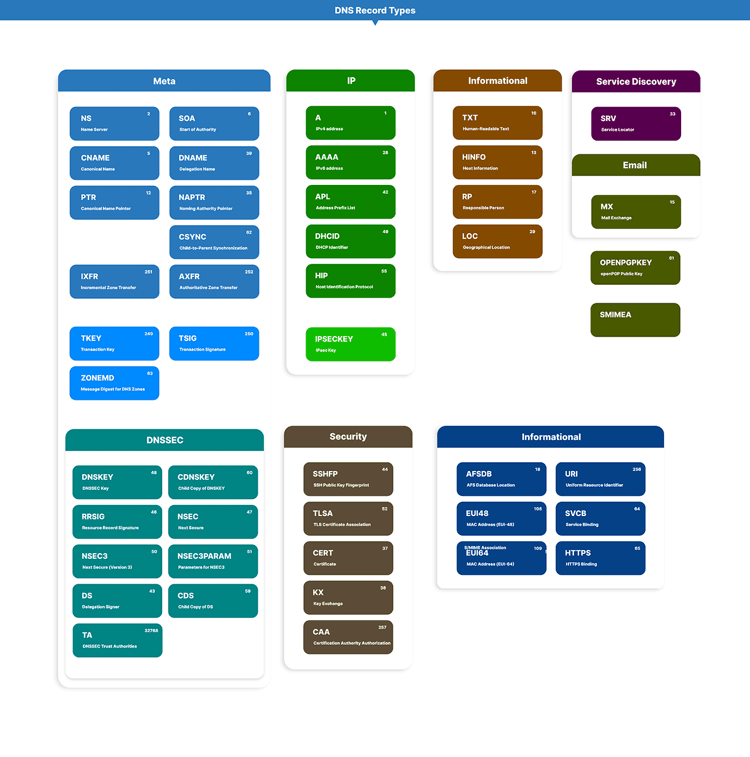
-
A – IPv4.
-
AAAA – IPv6.
-
AFSDB – Andrew File System Database record: maps a domain to its AFSDB address, or maps from a cell’s domain to authenticated name servers for that cell
-
APL – Address Prefix List: experimental record, specifies lists of address ranges
-
AXFR – Authoritative zone transfer: transfers the entire zone file from the primary nameserver to secondary nameservers
-
CAA – Certification Authority Authorization: specifies which certificate authorities (CAs) are allowed to issue certificates for a domain
-
CDNSKEY – Child copy of a DNSKEY: used to signal from one zone to its parent the desired contents of the zone’s DS record
-
CDS – Child copy of DS record
-
CERT – Cryptographic certificate: certificate record that stores certificates and their revocation lists
-
CNAME – Canonical name
-
CSYNC – Child-to-parent synchronization: specifies how a child zone in the DNS can publish a record to indicate to a parent that it can process certain records from the child zone
-
DHCID – DHCP identifier: used to associate DNS domains with DHCP clients using the domain names
-
DNAME – Delegation name: creates an alias for an entire subtree of the domain name tree (unlike the CNAME record, which creates an alias for a single name and not its subdomains)
-
DNSKEY – Cryptographic key for DNSSEC: specifies the DNSSEC key record
-
DS – Delegation Signer: The record used to identify the DNSSEC signing key of a delegated zone
-
EUI48 – EUI-48 address: used to store a single EUI-48 address in the DNS
-
EUI64 – EUI-64 address: used to store a single EUI-64 address in the DNS
-
HINFO – Host information: specifies general information about a host
-
HIP – Host Identification Protocol: uses the Host Identity Protocol and to separate the roles of an IP address (mostly used in mobile computing)
-
HTTPS – HTTPS binding: used to facilitate the lookup of information needed to make connections for origin resources (such as for HTTPS URLs)
-
IPSECKEY – Cryptographic key for IPsec: used to store public keys for use in IP security (IPsec) systems
-
IXFR – Incremental zone transfer: requests a zone transfer of the given zone, by specifying the differences from a previous serial number
-
KX – Key exchange: used with some cryptographic systems (not DNSSEC) to identify a key management agent for the associated domain name
-
LOC – Geolocation: specifies the physical location of network components
-
MX – Mail exchange
-
NAPTR – Naming Authority Pointer: allows regular expression-based rewriting of domains which can then be used as URIs, further domains to lookups, etc.
-
NS – Name Server
-
NSEC3 – Next secure (version 3): used for authenticated denial of existence for a name in DNSSEC
-
NSEC3PARAM – Parameters for NSEC3
-
OPENPGPKEY – Public key for OpenPGP: used for publishing and locating OpenPGP public keys in DNS for a specific email address
-
PTR – Canonical name pointer
-
RP – Responsible Person: specifies the mail address and description of the person responsible for the given zone or host
-
RRSIG – Resource record signature for DNSSEC: specifies digital signatures used in the DNSSEC authentication process
-
SMIMEA – S/MIME cert association: used to associate an end entity certificate or public key with the associated email address
-
SOA – Start of Authority
-
SSHFP – Secure Shell Fingerprint: helps identify SSH keys and contains fingerprints for public keys that are used for SSH
-
SVCB – Service binding: improves performance for clients that need to resolve many resources to access a domain.
-
SRV – Service record
-
TA – DNSSEC trust authorities: Part of a deployment proposal for DNSSEC without an signed DNS root
-
TKEY – Transaction signature key: authenticates DNS queries and responses using shared secret keys
-
TLSA – Certificate association for TLS: used to associate a TLS server certificate or public key with the domain name where the record is found
-
TSIG – Transaction signature: used to authenticate and secure DNS messages and server-to-server communication
-
TXT – Human-readable text
-
URI – Uniform Resource Identifier: used for publishing mappings from hostnames to URIs
-
WKS – Well-known services: specifies the well-known services supported by a particular protocol
-
ZONEMD – Message digest over zone data: provides a cryptographic message digest over DNS zone data at rest
Conclusion
With this overview of some of the less common, more unusual DNS records and record types, we hope we’ve shed some helpful light on how a website’s DNS works. Recognizing the number and functions of all the various records, record types, and mechanisms can be overwhelming, but understanding the basics will help guide you further into the world of DNS records: by detailing how the record sets are chosen, how they work, and how they can help you in the future.
Source of Article
